Security flaws in widely used libraries and platforms are continually discovered, potentially impacting thousands of applications at once. For instance, a severe bug (CVE-2025-27363) in the FreeType font rendering library recently allowed remote code execution by simply processing malicious fonts. Meanwhile, GitLab patched critical authentication bypass issues that could let attackers impersonate users. These incidents emphasize why developers must remain vigilant—keeping tools patched and integrating security checks into their development pipelines.
1. Recent High-Profile Incidents
1.1 FreeType Font Rendering Library
FreeType is ubiquitous in Linux distributions, embedded systems, and even some Windows or macOS software for font rendering. In early 2025, Meta’s security team discovered a critical flaw:
- CVE-2025-27363: A specially crafted font file could exploit a buffer overflow, allowing remote code execution.
- Impact: Nearly all major Linux distros (Ubuntu, Fedora, Debian) included a vulnerable FreeType version, forcing maintainers to release urgent patches.
- Developer Response: App authors using FreeType in their stack needed to push updated packages or container images quickly to avoid potential exploitation.

Why It Matters: This was a textbook example of a “low-level library” vulnerability being relevant across the entire software ecosystem. If you build on Linux or handle fonts in any capacity, ignoring FreeType updates could risk letting an attacker run arbitrary code on user systems—just by opening or rendering a malicious font.
1.2 GitLab Authentication Bypass
Shortly after the FreeType fiasco, GitLab confirmed and fixed major authentication bypass flaws in its self-hosted software:
- Critical Auth Issues: Attackers could impersonate legitimate users, potentially granting admin access.
- Timeline: Patched in an emergency release, with instructions for immediate upgrade.
- Widespread Usage: Thousands of organizations rely on GitLab for source code management and CI/CD. A compromised instance might let adversaries alter code or exfiltrate proprietary repositories.
Why It Matters: This type of vulnerability underscores the chain effect—if your version control or CI system is compromised, everything else is at risk. Attackers could push malicious commits or build scripts, leading to downstream supply chain attacks.
2. Common Patterns in These Vulnerabilities
- Core Dependencies: Libraries like FreeType are widely included in OS-level packages or embedded in other frameworks. Security issues often affect a broad user base, not just a small niche.
- Privileged Tools: GitLab or other DevOps platforms manage code and pipelines, making them prime targets. A single flaw can yield high-impact intrusions, from credential theft to unauthorized code pushes.
- Underestimated Attack Surfaces: Font rendering or authentication routines may not be top-of-mind for developers, yet they can be exploited creatively—reaffirming the principle that any system component can be an entry point.
3. Why It Matters for Developers
3.1 Urgency of Security Patches
When vulnerabilities surface, patching shouldn’t be postponed:
- Risk of Exploit: Proof-of-concept (PoC) code often circulates within days. Attackers actively scan for unpatched systems.
- Real-World Impact: Exploits could lead to remote code execution, data leaks, or entire environment compromises.
- Technical Debt: Unpatched software accumulates risk over time, making later fixes more complicated and expensive.
3.2 Evolving Attack Methods
Attackers increasingly look for single points of failure. A hidden bug in a widely used library or an authentication bypass in a popular DevOps tool can let them compromise many targets at once—supply chain attacks remain an escalating trend.
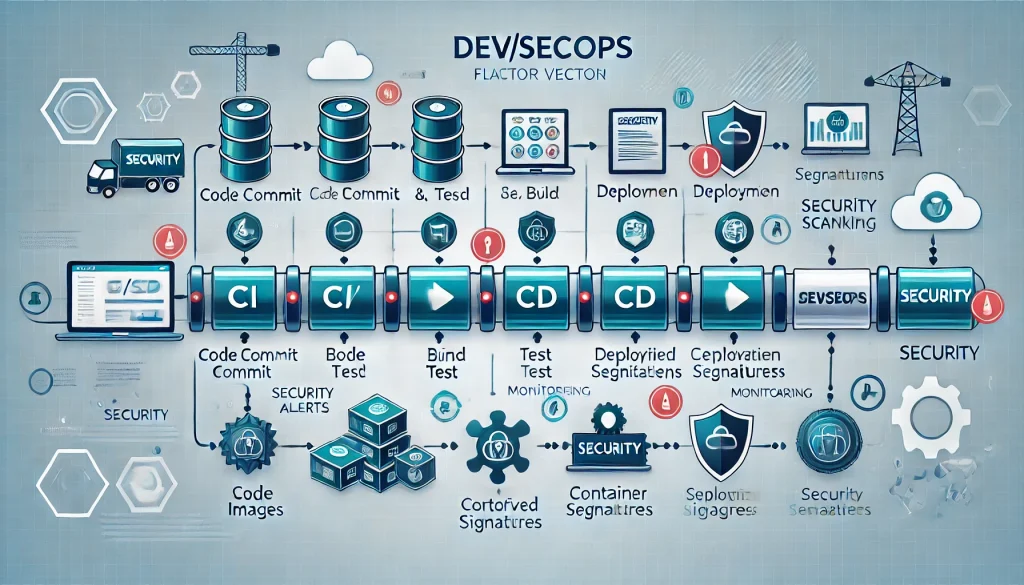
3.3 DevSecOps Emphasis
The industry is shifting to DevSecOps—where security steps integrate into all stages of development, from coding to release. Key practices include:
- Dependency Scanning: Tools like
npm audit,pip-audit, or Snyk for known vulnerability checks. - Container Image Scans: Ensuring base images and OS packages are up to date before deployment.
- Automated Patching: Setting up scheduled or triggered patch processes to minimize window of exposure.
4. Best Practices for Handling Critical Vulns

4.1 Continuous Monitoring
Subscribe to security advisories or vulnerability feeds (e.g., for Linux distros, GitLab, or major libraries). Tools like Dependabot or Renovate can automate dependency version checks and open pull requests when vulnerabilities appear.
4.2 Rapid Response Playbooks
Document the process for responding to major security incidents:
- Identify and Assess: Confirm which systems or apps rely on the compromised component.
- Mitigate: Turn off or isolate vulnerable services if needed.
- Patch: Deploy updated versions as soon as possible.
- Rotate Secrets: If credentials were at risk, change them to block attacker reuse.
- Audit Logs: Look for suspicious activity around the exploit timeframe.
4.3 Implement DevSecOps Pipelines
Adopt a pipeline that includes:
- Automated Vulnerability Scanners: Check code and dependencies each commit or nightly.
- CI Security Plugins: Tools that run unit tests for known exploit patterns or container misconfigurations.
- Infrastructure as Code: Keep track of server and container configs in Git to easily revert or patch them, ensuring consistent, traceable changes.
4.4 Culture of Security
Foster a mindset among developers that security is everyone’s responsibility—not just an afterthought for a separate team. Conduct internal training on reading CVEs, analyzing threats, and writing secure code.
5. Future Outlook
5.1 More Frequent Zero-Day Disclosures
As complex software stacks increase, so do zero-day vulnerabilities. Expect more “shockwaves” from core libraries like FreeType or widely used dev tools. Quick patch cycles and strong DevSecOps practices will be essential to reducing exposure.
5.2 Industry-Wide Collaboration
Open-source communities, vendors, and big tech players will work more closely to coordinate patches, share vulnerability information, and unify standards for secure pipelines. This collective effort aims to minimize the damage from large-scale critical flaws.
5.3 Security-First Development
With supply chain attacks and library compromises on the rise, developers who integrate security into everyday coding, testing, and deployment processes will be better equipped to handle new threats. Tools, training, and best practices are constantly improving, but a proactive approach is crucial.
Conclusion
Critical vulnerabilities in commonly used libraries, like FreeType, or platforms, like GitLab, present a stark reminder: no software component is immune from infiltration. For developers and organizations alike, the message is clear—stay up-to-date, patch promptly, and weave security checks into every stage of development. By embracing DevSecOps practices and maintaining a culture of vigilance, we can reduce the risk of large-scale breaches and safeguard both user data and internal infrastructure.
Key Takeaways:
- Widespread Impact: A single bug in a ubiquitous library can affect thousands of apps.
- Timely Patching: Immediate response to new vulnerabilities prevents known exploits from wreaking havoc.
- DevSecOps Integration: Automated scanning, container image checks, and continuous monitoring are now must-haves.
- Security Culture: Everyone on the team—from devs to ops—should be security-conscious, ensuring no vulnerability goes unnoticed.
In a rapidly evolving threat landscape, being proactive with patching and adopting robust DevSecOps techniques remain the best defenses against critical vulnerabilities.